Some people have reported a SQL injection vulnerability for jLinks r.php and ws.php file.
<?php $_REQUEST["option"]="com_jlinks";$_REQUEST["controller"]="redirect";$_REQUEST["link"]=$_REQUEST["l"];include("index.php");
We want to inform everyone that this is NOT a SQL injection, and here is why?
First all this file does is do a soft redirect with a shorter URL.Anyone with some PHP knowledge will realize that:This is a hard coded string, not variable here so no injection: $_REQUEST["option"]="com_jlinks";This is a hard coded string, not variable here so no injection: $_REQUEST["controller"]="redirect";This $_REQUEST["link"]=$_REQUEST["l"], simply takes the value of one $_REQUEST and put it into another one, again for simplicity of URL.All variables ( option, controller, redirect) ARE filtered afterward when read and used.
The reason why a crawler or other people might say that it is...
Sidebar
Joobi News
This is where we announce new releases, tutorials, tips and tricks and share what we're working on.
We have been testing Joomla 3.1 with jNews and all Joobi Applications and we have not found any compatibility issue.This means that all current users of jNews 8.0 and jCenter 2.3 can update their website to Joomla 3.1 without problems. You don't need to update your Applications, the current version works just fine.
For some reason you find issue using Joomla 3.1 environment please submit a ticket with the following subject "Joomla 3.1 -Issue Title-".
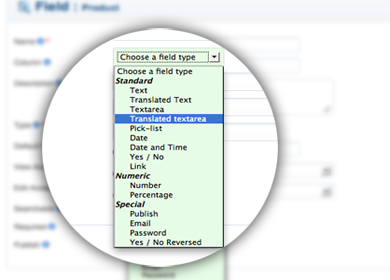
We are really delighted to present to you the new custom fields feature, not only for jMarket but for all Joobi Apps. It is now available in all eCommerce Apps and in jTickets.
We think the custom fields we developed are so powerful and flexible that it will make you rethink what custom fields should be. You will be able to for instance create native Tabs or make translatable text or text areas.
We just wanted to let everyone know that we are still working on updating all our site applications and contents, some of the contents may not be correct. Our new site replaces the 7-year-old one that was created during Acajoom days in 2005. Redesigning gives us a chance to address all the issues that have been stewing over since the beginning, along with a cleaning-up of spurious HTML code and hard-to-reach pages. We are doing our best to finalize the upgrading work as soon as possible. We apologize for any inconvenience this may have caused and appreciate everyone's patience
Keeping up with the pace, last month we did a great release with powerful features, this month we are making a new release with a lot of new features especially on the catalog and presentation of products.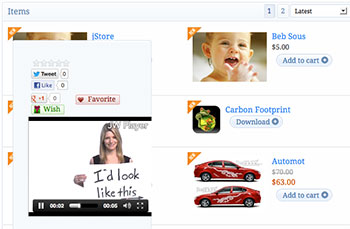

 Please wait...
Please wait...


